Block Cipher Operations
- Lecturer:
Prof. Dr. Michael Eichberg
- Version:
- 2023-10-19
- Based on:
Cryptography and Network Security - Principles and Practice, 8th Edition, William Stallings
Prof. Dr. Michael Eichberg
Cryptography and Network Security - Principles and Practice, 8th Edition, William Stallings
Observation: \(E(K_2,E(K_1,P)) = E(K_3,P)\) does not hold. I.e., the use of double DES results in a mapping that is not equivalent to a single DES encryption.
The meet-in-the-middle algorithm will attack this scheme. It does not depend on any particular property of DES but will work against any block encryption cipher.
The result is that a known plaintext attack against double-DES will succeed with an effort on the order \(2^{56}\) compared to \(2^{55}\) for a single DES.
Obvious counter to the meet-in-the-middle attack is to use three stages of encryption with three different keys.
This raises the cost of the meet-in-the-middle attack to \(2^{112}\), which is beyond what is practical.
Has the drawback of requiring a key length of \(56\,bits \times 3 = 168\,bits\), which may be somewhat unwieldy.
As an alternative Tuchman proposed a triple encryption method that uses only two keys.
3DES with two keys is a relatively popular alternative to DES and has been adopted for use in the key management standards ANSI X9.17 and ISO 8732.
Several attacks against 3DES with 2 keys have been developed, which are - however - still not practical.
Many researchers now feel that three-key 3DES is the preferred alternative.
Three-key 3DES has an effective key length of 168 bits and is defined as: \(C=E(K_3,D(K_2,E(K_1, P)))\)
Backward compatibility with DES is provided by putting: \(K_3 =K_2\) or \(K_1 =K_2\).
A technique for enhancing the effect of a cryptographic algorithm or adapting the algorithm for an application.
To apply a block cipher in a variety of applications, five modes of operation have been defined by NIST.
The five modes are intended to cover a wide variety of applications of encryption for which a block cipher could be used
These modes are intended for use with any symmetric block cipher, including 3DES and AES.
Mode |
Description |
Typical Application |
|---|---|---|
Electronic Codebook (ECB) |
Each block of plaintext bits is encoded independently using the same key. |
|
Cipher Block Chaining (CBC) |
The input to the encryption algorithm is the XOR of the next block of plaintext and the preceding block of ciphertext. |
|
Cipher Feedback (CFB) |
Input is processed s bits at a time. Preceding ciphertext is used as input to the encryption algorithm to produce pseudorandom output, which is XORed with plaintext to produce next unit of ciphertext. |
|
Output Feedback (OFB) |
Similar to CFB, except that the input to the encryption algorithm is the preceding encryption output, and full blocks are used. |
|
Counter (CTR) |
Each block of plaintext is XORed with an encrypted counter. The counter is incremented for each subsequent block. |
|
ECB-Tux - the linux pinguin encrypted using ECB mode.
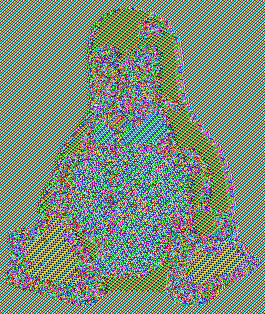
Criteria and properties for evaluating and constructing block cipher modes of operation that are superior to ECB.
Overhead
Error recovery
Error propagation
Diffusion
Security
For AES, DES, or any block cipher, encryption is performed on a block of b bits:
In the case of (3)DES \(b=64\)
In the case of AES \(b=128\)
can make use of hardware parallelization.
easily parallelizable in software.
the encryption of the counters
The i-th block of plaintext of ciphertext can be processed in random-access fashion.
as secure as the other modes
only the encryption algorithm is required.
Approved as an additional block cipher mode of operation by NIST in 2010 Mode is also an IEEE Standard, IEEE Std 1619-2007
Standard describes a method of encryption for data stored in sector- based devices where the threat model includes possible access to stored data by the adversary.
Has received widespread industry support
XTS-AES mode is based on the concept of a tweakable block cipher
General structure:
To compute the ciphertext a:
Plaintext
Symmetric key
Tweak
is required.
Tweak need not be kept secret; purpose is to provide variability.
The requirements for encrypting stored data, also referred to as “data at rest”, differ somewhat from those for transmitted data.
The P1619 standard was designed to have the following characteristics:
The ciphertext is freely available for an attacker.
The data layout is not changed on the storage medium and in transit.
Data are accessed in fixed sized blocks, independently from each other.
Encryption is performed in 16-byte blocks, independently from each other.
There are no other metadata used, except the location of the data blocks within the whole data set.
The same plaintext is encrypted to different ciphertexts at different locations, but always to the same ciphertext when written to the same location again.
A standard conformant device can be constructed for decryption of data encrypted by another standard conformant device.
Key: The key where: \(Key = Key_1\, ||\, Key_2\)
\(P_j\): The jth block of plaintext. All blocks have length 128 bits. A plaintext data unit, typically a disk sector, consists of a sequence of plaintext blocks.
\(C_j\): The jth block of ciphertext.
\(j\): The sequential number of the 128bit block inside the data unit.
\(i\): The value of the 128bit tweak.
\(\alpha\): A primitive element of GF(2^{128}) that corresponds to the polynomial \(x\) (i.e., 0000...0010)
\(\alpha^j\): \(\alpha\) multiplied by itself \(j\) times in \(GF(2^{128})\)
\(\oplus\) Bitwise XOR
\(\otimes\) Modular multiplication with binary coefficients modulo \(x^{128}+x^7+x^2+x+1\).